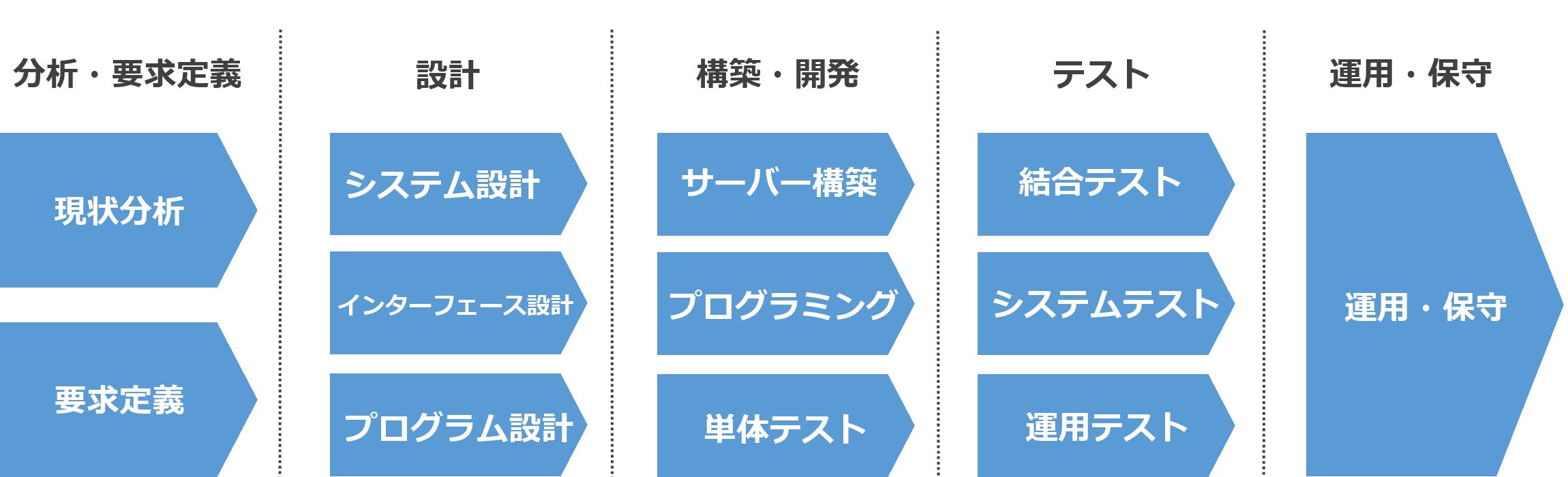
Keytool is a command line utility that allows you to manage and store encryption keys and certificates.
If you have Java installed on your system, you can use the keytool command to import CA certificates, list certificates, create self-signed certificates, save passphrases and public/private keys, and more. You can perform various operations.
Confused? Don’t worry. I will explain it clearly as you read.
Note that I will use Linux to test the commands and explain it a little more with an example.
Keytool commands are also available on Windows and macOS.
What is the Keytool command?
This is a key and certificate management utility. You can store private and public key pairs that are typically used to verify/authenticate access to a service.
Considering the title of this article, we can assume that this command is primarily used by system administrators and developers.
In most cases, this is true, but users can tweak the keytool command to store passphrases and private keys for authentication, encryption, and decryption purposes. So if you’re interested, try it out on your own system.
If you are unfamiliar with the concept of encryption keys, see the article on data encryption before trying the keytool command.
Additionally, you can also review examples of OpenSSL commands to understand how they differ and what you can do with them.
Create a self-signed certificate
keytool -genkeypair -alias <alias> -keypass <keypass> -validity <validity> -storepass <storepass>Unlike purchased SSL certificates, self-signed certificates are only used for development/testing purposes to use secure connections.
It can be generated using the keytool command syntax described above. For example:
keytool -genkeypair -alias -keypass passforkeystore -validity 365 -storepass passforkeystoreYou can use any name for the alias. as placeholder text. You can customize the validity and specify the keystore password by replacing ‘ passforkeystore ‘ in the above command.
Note that PKCS12 keystores only support one password . However, this is a useful keystore type that is not specific to Java.
If you require two different passwords for your keystore and certificate, you can explicitly tell the keytool command to use a different interface.
Please refer to the official documentation for more information.
If you continue to create, you will be asked for additional details to verify authenticity. It will look like this:
What is your first and last name?
[Unknown]: Ankush
What is the name of your organizational unit?
[Unknown]:
What is the name of your organization?
[Unknown]:
What is the name of your City or Locality?
[Unknown]: Bhubaneswar
What is the name of your State or Province?
[Unknown]: Odisha
What is the two-letter country code for this unit?
[Unknown]: 91
Is CN=Ankush, OU=, O=, L=Bhubaneswar, ST=Odisha, C=91 correct?
[no]: yes 
Creating a Java keystore and key pair
keytool -genkeypair -keyalg RSA -keysize 2048 -keystore keystore.jks -alias java -validity 3650 
Generate a Java keystore and import the certificate
Make sure you have a valid certificate or have previously generated one. Once completed, you can import it to generate a Java keystore.
keytool -importcert -file test.crt -keystore truststore.jks -alias 
Generate a key pair to the default keystore using a subject
You can quickly generate a key pair (for example, named “ca”) using the following command:
keytool -alias ca -dname CN=CA -genkeypair 
Create a chain of signed certificates
Suppose you have created a key pair ca and ca1. You can create a chain of signed certificates where CA signs CA1 using the following command:
keytool -alias ca1 -certreq keytool -alias ca -gencert -ext san=dns:ca1 keytool -alias ca1 -importcertTwo more key pairs, ca1 and ca2, can be used to complete the chain. Here, ca1 signs ca2.
Importing a certificate
If you want to import the certificate from an available file, you can do the following:
keystool -import -alias -file server.cerCreate a certificate signing request (CSR) for an existing keystore
Considering you have already created a keystore, you can generate a CSR.
keytool -certreq -keyalg rsa -keystore keystore.jks -alias server -file .csrListing certificates stored in Java keystore
A keystore can contain multiple entries for certificates. Assuming you are checking the list of certificates in the ” keystore.jks ” database, you should type:
keytool -v -list -keystore keystore.jksThe output in this case would be:
keytool -v -list -keystore keystore.jks
Enter keystore password:
Keystore type: PKCS12
Keystore provider: SUN
Your keystore contains 2 entries
Alias name: cert
Creation date: 16-Nov-2022
Entry type: PrivateKeyEntry
Certificate chain length: 1
Certificate[1]:
Owner: CN=Ankush, OU=Geek, O=, L=Bhubaneswar, ST=od, C=91
Issuer: CN=Ankush, OU=Geek, O=, L=Bhubaneswar, ST=od, C=91
Serial number: a0b9a99
Valid from: Wed Nov 16 09:42:37 IST 2022 until: Sat Nov 13 09:42:37 IST 2032
Certificate fingerprints:
SHA1: 23:7C:65:A7:A6:84:18:F8:45:04:92:DF:D4:BB:0F:91:6D:A5:C5:BE
SHA256: C0:25:ED:B8:CF:1A:E6:E1:C5:75:A8:10:8F:CD:BE:42:26:96:9C:9A:FA:74:65:07:71:06:9A:2C:F5:80:FE:7F
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3Check the contents of a single certificate
Considering you already have a generated certificate, you can check the certificate details using the following command:
keytool -v -printcert -file server.crtView Java keystore certificate
You can list all certificates from the keystore database. The command will look like this:
keytool -v -list -keystore keystore.jksView keystores using aliases and keystores
If you want to verify the keystore using the alias name you set when creating the keystore, type:
keytool -v -list -keystore keystore.jks -alias serverListing certificates in keystore
If you want to check the certificates stored in the default keystore, use the following command:
keytool -list -storepass passforkeystoreYou need to replace ” passforkeystore ” with the password you configured.
Viewing certificate information
If you need to check the details of a single certificate, you can use its alias without specifying the keystone database.
The situation is as follows.
keytool -list -v -alias -storepass passforkeystoreView certificate in PEM format
PEM is one of the most common formats for certificates and encryption keys. If you want to check the certificate in PEM, type:
keytool -v -printcert -file .crt -rfcChange the Java keystore password
If you have already created a password for your Java keystore, you can change it using the following command:
keytool -delete -alias -keystore keystore.jksDelete a certificate from the Java keystore
You can specify and delete Java keystores and their aliases. for example:
keytool -delete -alias -keystore keystore.jksExplore commands and get help
This command has several arguments and extensions to perform various operations. Depending on your use case, you may or may not need to use all of them.
So if you want to know more about command options, you can always type:
keytool -helpIn either case, if you are using a Linux terminal, we recommend reading the man page with the following command:
man keytoolYou can get all the details you need about the keytool command using the man command.
So, make this superpower yours to learn all you can about it.
summary
File paths and other customization options may differ slightly depending on the platform you are using. Also see the Oracle documentation for standardized options.
Keytool is a great tool for a variety of tasks. Give it a try and see what you can do!
You can also explore some Linux commands to keep your system running optimally.




![How to set up a Raspberry Pi web server in 2021 [Guide]](https://i0.wp.com/pcmanabu.com/wp-content/uploads/2019/10/web-server-02-309x198.png?w=1200&resize=1200,0&ssl=1)












































