Although SSO is a great productivity and security tool, it leaves password-related security gaps.
Single sign-on (SSO) solutions were rapidly gaining popularity even before the coronavirus disease (COVID-19) pandemic put a huge demand on the cloud. Today, SSO is more popular than ever because it provides convenience and security benefits for organizations with distributed workforces, including:
- Employees only need to remember one password. Eliminating “password fatigue” is one of the biggest drivers for SSO adoption. Instead of using different passwords for each app or service, employees only need to remember a password for single sign-on.
- You only need to enter your password once a day. Not only do you not have to remember multiple passwords, but your employees also don’t have to enter multiple passwords during work hours. By entering your SSO password once at the beginning of your workday, you no longer waste time entering passwords throughout your workday.
- Cut your help desk ticket in half. Gartner Group estimates that password resets account for up to 50% of help desk tickets. SSO promises to virtually eliminate these tickets, allowing support employees to spend more time helping end users with more complex issues. It will be.
- Easily implement identity access and management (IAM). SSO reduces the complexity of configuring authentication and access controls, enables faster and simpler deployment of IAM solutions, and enables a faster path to a zero trust environment.
- Compliance reporting made easier. Many popular compliance frameworks require a user audit trail of user sign-on data. SSO makes it easy to include this data in compliance reports.
Disadvantages of SSO: Password-related security gaps
The purpose of SSO is to facilitate access to resources. This is great from a productivity standpoint, but not from a security standpoint.
- A single password represents a single point of failure. If an employee loses or forgets the password for one account, they are locked out of that account. If you forget your SSO password, you’ll be locked out of all your accounts. Even more concerning, once cybercriminals have SSO passwords, they can potentially compromise all of your employees’ work-related accounts. Verizon estimates that over 80% of successful data breaches are due to password compromise, which is a major drawback.
- Traditional line-of-business (LOB) apps don’t support SSO. Even though the COVID-19 pandemic accelerated digital transformation efforts by several years, most organizations still use at least some legacy LOB apps that don’t support SSO. They are so old that it is not practical to modernize them. These are so specialized that replacing them is also impractical.
- Not all modern apps support SSO. It’s not just traditional apps that are a problem. Many modern apps and services, especially desktop apps, also don’t support SSO. An organization’s SSO implementation rarely covers all the apps used by employees. Especially in large companies, there may be literally hundreds of apps in use.
- Different apps may use different SSO protocols. Employees may need to use an app that uses a different protocol than the one used by your organization’s identity provider (IdP). For example, if your IdP uses the SAML protocol, your SSO solution won’t support apps that use OAuth.
- You have no control over your users’ password habits. SSO deployments do not provide visibility into poor password security practices. Employees can choose weak or previously compromised passwords for SSO logins, or reuse passwords used for multiple additional accounts. You could potentially do the same for any apps that your SSO deployment doesn’t support. We may also share your password with unauthorized third parties.
- There is no protection for privileged users or sessions. Typically, users must enter additional credentials to access particularly sensitive systems or data, but the purpose of SSO is to give users a single authentication pass for all access.
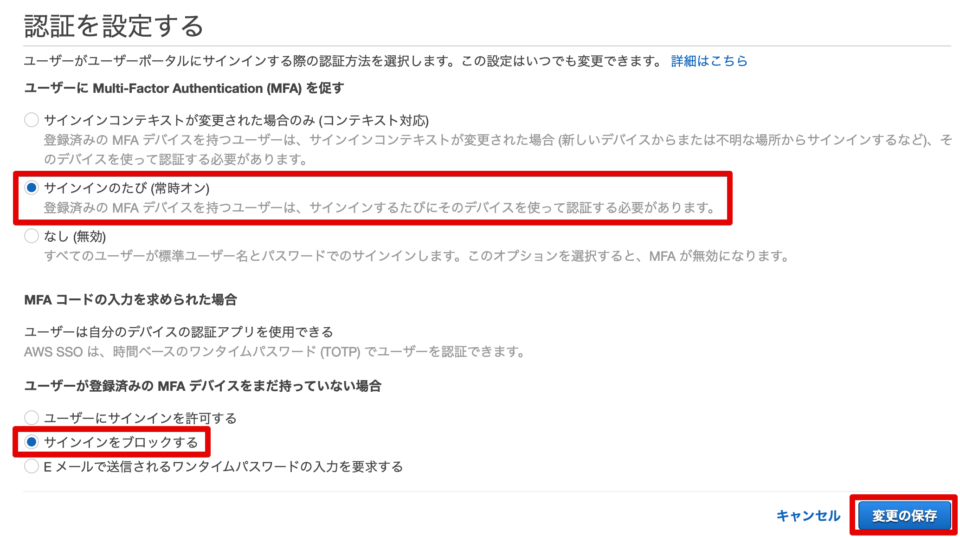
4 ways to close the password-related security gap left by SSO

Despite these risks, security-minded organizations should not abandon SSO implementation. There is no one-size-fits-all security solution. By combining SSO solutions with complementary technologies, organizations can close password-related security gaps while retaining the productivity and ease-of-use benefits of SSO.
#1. Implement role-based access control (RBAC) for least privilege access for all users.
The principle of least privilege states that users should have access to only the lowest level of system privileges to perform their jobs and no more, reducing the risk of potential attacks on an organization. Important for reducing the target area. RBAC simplifies the assignment and management of access control levels.
To make RBAC role assignments easier to manage, avoid assigning roles directly to users. Instead, create groups, assign permissions to the groups, and add users to the groups accordingly. This not only minimizes the number of role assignments, but also saves time when you need to change permissions for all users in a group. Make sure your groups are reusable and avoid creating too many custom roles.
#2. Implement Privileged Access Management (PAM) using Privileged Session Management (PSM) for privileged users
Unlike SSO, which focuses on making access as easy as possible, PAM focuses on restricting access to a company’s most sensitive systems and data. Organizations use PAM to restrict and monitor access to their most critical and sensitive systems. Privileged users are typically high-level internal stakeholders such as IT administrators, security administrators, and executives, but trusted vendors and partners may also fall into this category.
PAM and PSM work together. While PAM controls user access to sensitive resources, PSM controls, monitors, and records privileged user sessions to prevent privileged users from abusing their access. Typical PSM monitoring and recording is very detailed and includes keystrokes, mouse movements, and screenshots. In addition to ensuring security, PSM audit trails are required by several compliance frameworks such as HIPAA, PCI DSS, FISMA, and SOX.
#3. Implement multi-factor authentication for all apps and services that support it
Multi-factor authentication (2FA) is one of the strongest defenses against password compromise. Even if a cybercriminal compromises your password, they can’t use it without a second authentication factor. 2FA protects all users, from those with minimal system access to your company’s most privileged users. Strengthen zero trust by allowing organizations to authenticate user identities.
Some organizations are hesitant to implement 2FA, fearing that forcing employees through additional login steps will reduce productivity. This problem can be easily solved by combining 2FA with a modern password security solution. This solution allows users to save their 2FA credentials along with their passwords. .
#4. Deploy an enterprise password security and encryption platform company-wide.
Our password security and encryption platform allows employees to securely store all their login credentials in one central, private encrypted repository. Similar to SSO, users remember only one “master password,” which is used to access all of their credentials in a digital repository.
Unlike SSO, a good enterprise password security and encryption platform is designed to work with all services and apps, including legacy apps. These include additional features such as automatic generation of strong passwords and autofill tools. It also allows IT administrators to fully understand users’ password habits and enforce password security policies. Be sure to deploy an enterprise-grade password security and encryption platform that seamlessly integrates with your existing SSO deployment and provides support for RBAC, 2FA, auditing, and event reporting.
SSO poses a security risk only if an organization considers it a standalone solution. By recognizing the password-related security gaps inherent in SSO and compensating for them by implementing complementary technologies such as 2FA, RBAC, PAM/PSM, and password security and encryption platforms, organizations can improve efficiency. , which can improve the end user experience. Protect yourself from password-related cyber attacks.
Written by Teresa Rosal




![How to set up a Raspberry Pi web server in 2021 [Guide]](https://i0.wp.com/pcmanabu.com/wp-content/uploads/2019/10/web-server-02-309x198.png?w=1200&resize=1200,0&ssl=1)












































